Introduction
Hello, everyone! My name is Ashton Briscoe, and I am a Microsoft Security Engineer with a passion for solving complex problems and enhancing user experiences. Recently, I had the opportunity to work on an intriguing project that involved migrating a customer's identity management system from CyberArk to Microsoft Entra ID. This project presented a unique challenge: ensuring a seamless transition for users without compromising security.
In this blog post, I will walk you through the problem we faced, the innovative solution we implemented, and the positive outcomes we achieved. Whether you are an IT professional, a security enthusiast, or simply curious about identity management, I hope you find this journey as fascinating as I did.
The Challenge
As we began the migration planning, we quickly encountered a significant issue: CyberArk does not sync users' passwords to Microsoft Entra ID. This meant that no passwords were stored in Entra ID, posing a risk of users being locked out if federation were to break before setting new passwords. The customer initially requested a spreadsheet with all user passwords, but as a Security Engineer, I knew this approach was not secure. Another issue is that when the Microsoft Entra ID authentication flow is federated, neither users nor admins of federated domains are allowed to change their passwords in Microsoft Entra ID. They encounter an error message. Here is how we tackled this challenge.
Customer's Request
During the migration planning, the customer requested that we create a spreadsheet containing all user passwords. While this might seem like a straightforward solution, it raised several significant security concerns. The customer also requested that users not be prompted to change their passwords during the first login after the federation is broken and Entra ID authentication is set back to “managed.”
Security Concerns
- Risk of Data Breach: Storing passwords in a spreadsheet, even temporarily, poses a high risk of data breach. If the spreadsheet were to fall into the wrong hands, inauthorized access to sensitive information. could result
- Compliance Issues: Many regulatory frameworks, such as GDPR and HIPAA, have strict guidelines on how sensitive data, including passwords, should be handled. Storing passwords in an unencrypted format would likely violate these regulations, leading to potential legal repercussions.
- User Trust: Users trust that their credentials are being handled securely. CStoringpasswords in an insecure manner could compromise this trust, damaging the organization's reputation and eroding user confidence.
- Best Practices: As a Security Engineer, it is crucial to adhere to best practices for password management. This includes never storing passwords in plain text and ensuring that any password handling is done securely and in compliance with industry standards.
The Solution
Faced with the challenge of securely migrating user passwords without storing them insecurely, I proposed an innovative solution: building a PHP website that updates user passwords using the Microsoft Graph API. This approach allows users to be in full control of their password updates.
Technical Details
- Microsoft Graph API: The Microsoft Graph API is a powerful tool for developers to interact with various Microsoft services. Using this API, we could programmatically update user passwords in Microsoft Entra ID without needing to know the existing passwords.
- PHP Website: I developed a PHP-based web application that served as the interface for this process. The website was designed to be user-friendly and secure, ensuring that only authorized administrators could access it.
- Password Update Process:
-
- Authentication: The website authenticated users using OAuth 2.0, ensuring secure access to the Microsoft Graph API.
-
- User Selection: To avoid abuse, a one-time execution file was logged to the server. When a user tried again, the website blocked their access. Only users who were members of a dynamic group matching the federated domain were allowed to use the website.
-
- Password Generation: The user was prompted with a simple webpage and two input fields for their password.
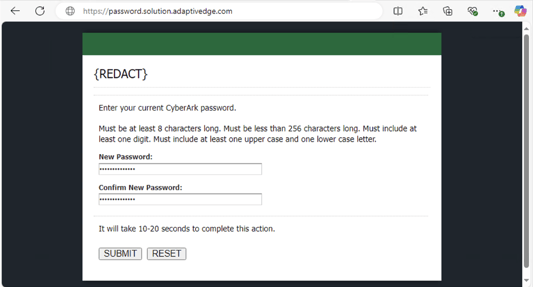
-
- Validation: The password is securely sent back to the server, and the PHP application validates that the passwords match.
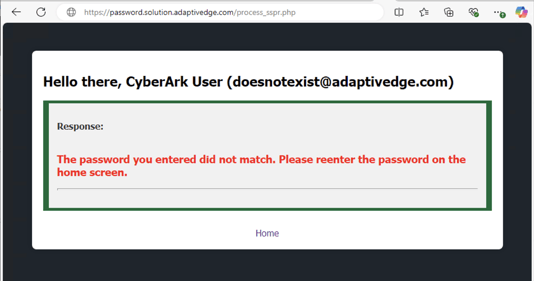
-
- API Call: The website updated the passwords in Microsoft Entra ID using the Microsoft Graph API and certificate-based authentication. The password is updated according to the input data submitted by the user. The property “forceChangePasswordNextSignIn = $false” is also included in the request, preventing the password change prompt from being presented to the user. In return, a response from the API or server is presented to the user.


Challenges and Solutions
- API Permissions: One of the initial challenges was configuring the correct permissions for the Microsoft Graph API. We needed to ensure that the application had the necessary permissions to update passwords without granting excessive access. This was achieved by carefully selecting the least-privilege permissions required for the task. The application's scope for password profile management utilizes an undocumented API endpoint. Finding that one out was quite interesting.
- Application: User-PasswordProfile.ReadWrite.All
- Delegated: offline_access, openid, profile, User.Read, email

- Security Measures: To protect the integrity of the password update process, several security measures were implemented:
- HTTPS: The website was hosted over HTTPS to encrypt data in transit.
- Input Validation: All inputs were validated to prevent injection attacks. Cloudflare handled most of this mitigation.
- Logging and Monitoring: Detailed logs were maintained to monitor the password update process and detect anomalies. If any occurred, users were also presented with a dynamic error message
- User Communication: To ensure a smooth transition, we communicated with users about the upcoming changes. Users were informed about the new authentication flow and the need to add their password to Microsoft Entra ID before the CyberArk federation was removed.
- Check User Run Once: To allow the customer to quickly view who executed a password change, a simple PHP webpage was added to pull the cache count and present a table. I even sorted the table by the “Password Last Modified” column.

- Check Users' Last Password Change: The customer requested to see who had a blank password profile or a last password update on or before September 20, 2024. Any users on the list risked being locked out. This also helped quickly determine who required additional reminders.

- User Enters Incorrect Data or API Error Occurs: A dynamic error message was presented to the user with the issue and ways to resolve it. The example in the snippet below can occur due to an issue when the UPN is changed, and the second invocation executes based on the new temporary UPN value. It's a good thing we did not run into this issue.
- Unable to Update Federated Users' Password: Before the password profile is deployed, the user's current federation configuration is quickly broken. This is done by changing the current UPN from the federated domain back to the primary domain, sending the updated password profile, and then immediately switching the UPN back to its original value.

Implementation Steps
- Setup: Installed and configured a web server with PHP and the necessary libraries for interacting with the Microsoft Graph API. Additionally, PowerShell 7 was installed. Yes, I work magic in the background with both PHP and PowerShell to provide the necessary results.
- Development: Developed the PHP website, focusing on secure coding practices and user-friendly design. Developed PowerShell scripts to process the majority of the server-side API calls.
- Testing: Conducted thorough testing to ensure the website and PowerShell scripts functioned correctly and securely.
- Deployment: The website was deployed in a secure environment. It ran on a simple Windows 11 Azure VM with IIS as the web server and FastCgiModule handler for PHP integration.
- Web Access: The Microsoft Entra application proxy was installed for remote web access. Since the customer uses Cloudflare for DNS, we also turned on the Cloudflare DNS proxy feature, ensuring the website's information was never revealed in the public DNS space. Cloudflare's advanced attack protection secured the website. All HTTP (port 80) connections were forcefully redirected to HTTPS (port 443) for a secure connection. This was done at the IIS server MS App Proxy and Cloudflare levels.
Results
Implementing the PHP website using the Microsoft Graph API was a resounding success. We were able to update the passwords for all users in Microsoft Entra ID without knowing their existing passwords, ensuring a seamless transition. In fact, users were in full control of their desired password.
- Successful Password Migration: The solution allowed us to update passwords for over 300 users within a few days, significantly reducing the risk of user lockouts.
- Enhanced Security: We maintained high security standards by avoiding storing passwords in a spreadsheet. A security audit validated our approach and confirmed the solution adhered to best practices and regulatory requirements.
- User Experience: The transition was smooth, with no disruption to user access. User feedback was overwhelmingly positive, with many appreciating the seamless process and clear communication.
- Customer Satisfaction: The customer was delighted with the solution and appreciated our innovative approach and commitment to security. One of the customer's IT Directors remarked, "This solution not only met our needs but also ensured our users' credentials were handled securely."
- Lessons Learned: This project reinforced the importance of secure password management and the value of innovative thinking in solving complex problems. We also learned the importance of clear communication with users during such transitions.
Conclusion
In this project, we faced a significant challenge in migrating user passwords securely from CyberArk to Microsoft Entra ID. By developing a PHP website that utilized the Microsoft Graph API, we provided a seamless and secure solution that met the customer's needs and enhanced the user experience.
This project reinforced the importance of innovative thinking and adherence to security best practices. It also highlighted the value of clear communication and collaboration with customers to achieve successful outcomes.
I hope you found this journey insightful and inspiring. I would love to hear from you if you have any questions, thoughts, or similar experiences. Feel free to leave a comment below or reach out to me directly.
Thank you for reading!

