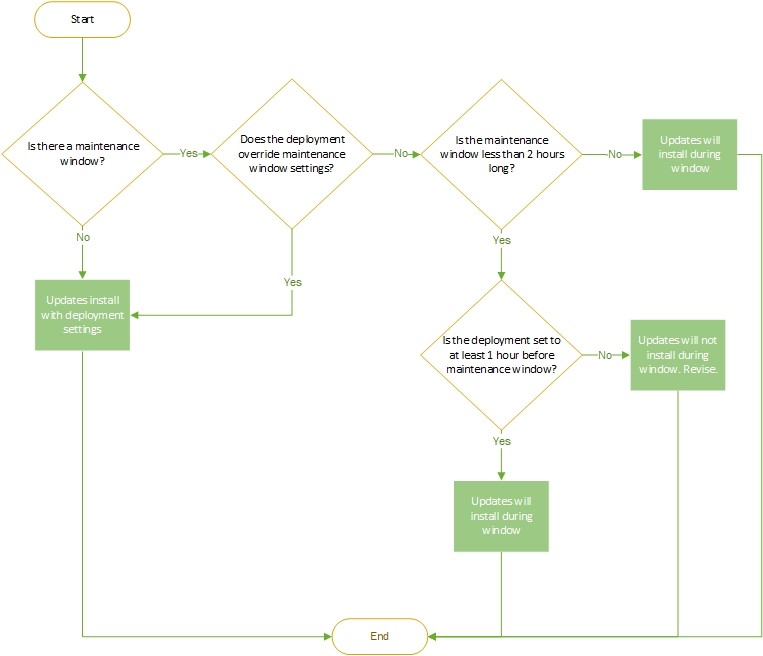
In a recent alert, the U.S. Computer Emergency Readiness Team (US-CERT) said that about 85 percent of successful security breaches involve systems that have not been patched. A recent study by research firm Voke Media found that 82 percent of security breaches since 2015 occurred due to unapplied patches that had been available for up to a year.
Read More
Tags:
adaptivedge,
SCCM,
software update,
Microsoft,
SUP
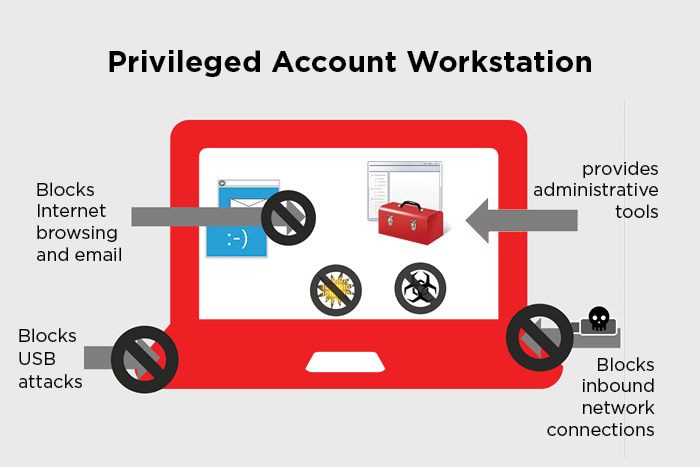
In Part 1 of this post, we examined how two Microsoft solutions, Privileged Access Workstation (PAW) and Local Administrator Password Solution (LAPS), protect privileged accounts and the data and applications they use. PAW is capable of distinguishing privileged administrative accounts from normal user accounts. When a privileged account is recognized, PAW creates a hardened physical environment for sensitive tasks while preventing high-risk activity. LAPS automatically generates, encrypts and randomizes passwords based on security policies and simplifies password management.
Read More
Tags:
adaptivedge,
cybersecurity,
PAWS,
identity management,
privileged accounts
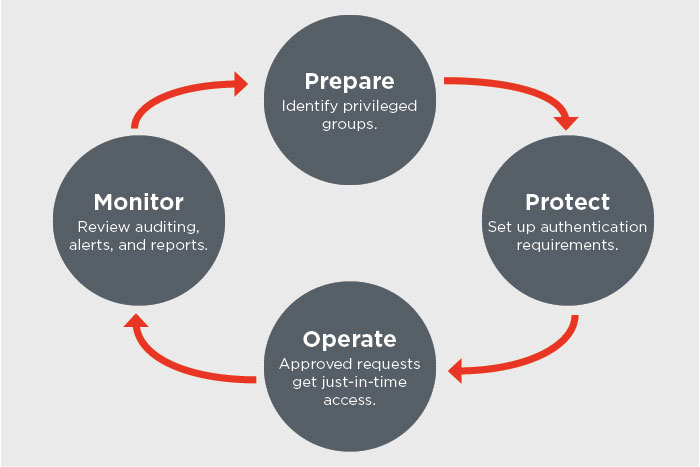
In a previous post, we discussed how to protect privileged accounts using robust identity management and authentication mechanisms to control access to company resources on a more granular level. We introduced three tools from Microsoft that can keep privileged accounts from being compromised – Microsoft Privileged Access Workstation (PAW), Local Administrator Password Solution (LAPS) and Privileged Access Management (PAM). In this post, we’ll take a deeper dive into PAW and LAPS.
Read More
Tags:
adaptivedge,
PAWS,
LAPS,
identity management,
privileged accounts
Over the last several posts, we’ve been discussing the need for a modern security strategy that protects the “identity perimeter” with special emphasis on securing privileged accounts. We also explained how user and entity behavior analytics can break the cyberattack chain by identifying and mitigating insider threats and compromised user credentials.
Read More
Tags:
adaptivedge,
cybersecurity,
identity management,
privileged accounts,
data loss prevention,
identity perimeter
In the military, the term “attack chain” or “kill chain” is used to describe how an attack is structured and executed, from identification of a target to selection of an appropriate weapon to the use of that weapon on the target. Reconnaissance operations are employed throughout the chain to monitor the movement and defense capabilities of the target and evaluate the impact of the attack.
Read More
Tags:
adaptivedge,
cybersecurity,
identity,
phishing,
UEBA,
cyberattack,
security
In our last post, we explained that identity has become the new perimeter in today’s cloud-based, mobile-enabled environment. It’s no longer possible to maintain IT assets and applications behind a firewall. Organizations must implement robust identity management and authentication mechanisms to ensure that only authorized users gain access to resources.
Read More
Tags:
Active Directory,
adaptivedge,
Azure,
cybersecurity,
privileged accounts,
Microsoft
The days when users accessed corporate applications and data via desktops at the office are long past. Mobile devices enable anytime, anywhere access to both internal and cloud-based resources. The traditional network perimeter no longer exists.
Read More
Tags:
Active Directory,
adaptivedge,
microsoft azure,
cybersecurity,
Microsoft,
security
Cybersecurity is a top priority for organizations. According to IDG’s 2017 State of the CIO Report, 32 percent of CEOs want their CIOs to focus on upgrading the IT security infrastructure. That’s the same number that are wanting their CIOs to help drive revenue growth. What’s more, 51 percent of survey respondents said their cybersecurity strategy and overall IT strategy were tightly integrated. On average, 12 percent of the IT budget is earmarked for cybersecurity.
Read More
Tags:
adaptivedge,
Azure,
microsoft azure,
cybersecurity
This webinar, given by our Senior Managing Partner, Steve Soper, provides a high-level overview of Microsoft Application deployment pros and cons of Cloud, On-Premise and Hybrid topologies. The session will cover Exchange, SharePoint, Skype for Business (Lync) and Active Directory along with their cloud counterparts in Office 365 and Azure. Learn some of the critical decision points and criteria to consider in developing your go-forward Microsoft application strategy.
Read More
Tags:
Adaptive Edge,
adaptivedge,
Private Cloud,
Cloud,
microsoft gold partner,
Office 365
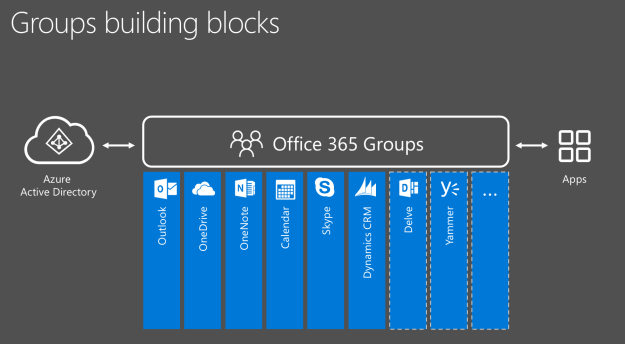
I would like to discuss today configuring Office 365 Groups with on-premises Exchange Hybrid. Office 365 Groups is the new type of group that allows its members to collaborate efficiently through a variety of services, such as SharePoint Team Site, Yammer, Shared OneNote Notebook, Shared Calendar, Planner, and SharePoint Document Library.
Read More
Tags:
adaptivedge,
Coexistence,
Hybrid,
O365,
Office 365 Groups,
SKU,
Azure,
Enterprise,
Group Writeback,
microsoft gold partner,
Office 365,
PowerShell,
Unified Groups