Many organizations migrate their files to the Microsoft Cloud as a way to minimize the long-term costs of maintaining or upgrading on-premises legacy servers. Microsoft Cloud platforms also offer flexibility and scalability for companies that are growing, merging, or otherwise transforming. The cloud is the future of data storage.
However, when migrating content from an on-premises environment to the Microsoft Cloud, security, compliance, and governance are always top of mind. While on-premises environments are typically secured via network access controls, securing data in the cloud requires an entirely different set of procedures.
In this blog post, I’ll cover the security risks faced by companies with on-premises file servers, how a file server migration to Microsoft 365 can mitigate these risks, and what is required to ensure a secure file server migration to the Microsoft cloud.
Why legacy information architecture frameworks pose security risks
Organizations that operate their own IT environments using an on-site data center safeguard their data physically with concrete walls, cages, bolts, and even temperature regulation. Digitally, they utilize firewalls, VPN access, and encryption and assume the data is protected. However, this is often a false sense of security.
That’s because IT departments often overlook or ignore the serious security risks these legacy systems pose: the very real threat that employees who have access to files in the data center (or on SharePoint or Dropbox), can do anything they want with them. They can download them, they can save them to hard drives, they can send them outside the company as unsecured email attachments.
Another concerning trend in larger organizations is shadow IT security risks, where individual departments go outside the company’s IT organization to deploy the technology they want, but may not be approved. This is another way to breach the company’s security systems.
Many times the measures put in place to keep data compliant and secure actually offer very little cyber safety in an archaic security model.
At the same time, the world has changed; companies rely on collaboration now more than ever. Daily communication with customers, vendors, partners, and other external collaborators requires the instantaneous sharing of information. Add to that the COVID-19 pandemic, which accelerated the move to remote work, and it’s clear that businesses need to enable their employees to securely access data and collaborate if they are going to thrive.
While many businesses acted quickly to enable remote work during the pandemic, they now are tasked with making these changes permanent. According to the Pew Research Center, employees who pivoted during the pandemic to work from home have chosen to continue working remotely. Employers need to incorporate sustainable, long-term solutions for accessing, sharing, and securing data.
How to address the risks of shadow IT security and false protection
Moving data to Microsoft 365 addresses both the false sense of protection and the need for internal and external collaboration that most companies are facing. But implementing a new way of storing, sharing, and managing data is a complex endeavor and requires a strong plan – and partner – particularly around data security and compliance. That’s because companies have years’ or even decades’ worth of data on their servers and many of these files contain sensitive or confidential information.
In our work helping clients migrate their data to the Microsoft Cloud, we have seen that if the project is executed thoughtfully and correctly, the move to the cloud can not only address false protection, mitigate the shadow IT security risks, and enable collaboration, it can also be an opportunity to add security and compliance safeguards.
Conducting a Microsoft 365 security assessment
The best way to ensure there are controls and policies around data security when migrating to the cloud is to start with a Microsoft 365 Security Assessment.
A Microsoft 365 Security Assessment is a review of the security objectives and requirements of your Office 365 deployment from a security standpoint. Then, based on an analysis of security tools run and discovery in your environment, you get remediation recommendations in a customized, prioritized, and actionable roadmap to secure your deployment to the Microsoft Cloud. After the assessment, it’s critical to identify the sensitive data before protecting it through data classification and labeling.
A security assessment should incorporate the following components:
- Quantitative Assessment. To identify sensitive data, we start with a quantitative assessment by running an automated security scan using Microsoft’s Azure Information Protection (“AIP”) Scanner and following the steps in a proprietary 365 Microsoft File Server Migration Playbook. Leveraging Microsoft Power BI, we help customers understand what’s involved in the migration by providing a dynamic data visualization of the content by date, file types, authors, and relevance.
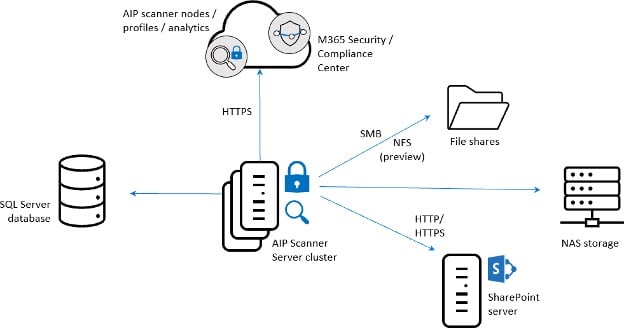
- Annotation process. Rounding out the technical scan is a human-led annotation process where internal content reviewers identify files that are sensitive or subject to regulatory requirements. We also interview key stakeholders to get qualitative information, add context, and address any files excluded from the scan. Each industry also potentially stores confidential data. Take healthcare providers, who must comply with HIPAA regulations. General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA) and other pending regulations also have ramifications for how and where data is stored. Some of this information is merely “sensitive” and could potentially damage a company’s reputation if it leaked. But if other “confidential” information gets out, that could lead to lawsuits or worse. This is a risk most organizations simply cannot afford to take.
- Content security policy analysis. Once you’ve identified the sensitive information you must label it accurately in order to protect it. Microsoft 365 has its own sensitivity labels that cover broad categories including public, general, confidential, and highly confidential. However, labels are customizable so you can encrypt files, require permission to open, restrict printing, or more. You can also add retention labels to delete content or retain it for compliance issues.
- Review/create data classification standards. Perhaps the most important, yet often overlooked, aspect of labeling data during a server migration is reviewing and/or creating data classification standards. Often, the content in scope for the data file migration requires a content security policy analysis to determine whether you need to expand or adjust your existing policies. A good data classification policy will be customized to your organization and generally includes the scope, roles and responsibilities, process for classification, impact level, timeline for review, and anything else that helps you clearly define how to secure sensitive data in your IT environment.
If your organization does not have a well-defined data classification policy then that’s the first place to start. Working with your legal and information security teams, AdaptivEdge can help lead the effort to create and document a data classification policy that meets your compliance requirements. Based on the data classification policy, AdaptivEdge will collaborate with you to analyze and design Microsoft 365 policies around:
- Sensitivity Labels
- Retention Labels
- Data Loss Prevention (DLP)
- Azure Information Protection (AIP)
- Azure AD Conditional Access
Data classification is critical work in a file server migration. AdaptivEdge brings experience, attention to detail, and a deep technical understanding to ensure your move isn’t just a “lift & shift” but that the content is migrated in a way that optimizes your information architecture framework and provides a solid foundation for future growth and secure collaboration.
How can an information architecture consultant best help with a file server migration?
A file server migration can be disruptive, but the disruption is temporary. And the results can be transformative from both a data protection and a business enablement perspective.
The reasons for moving to the Microsoft Cloud are to save money and time, enable the sharing of data in a fast and secure way, and retain control of your IT infrastructure.
Data protection is another critical benefit of the Microsoft Cloud. Security and compliance policies are with your files, wherever they go. Permissions and encryption can be applied at the file level so that successful authentication is required to de-encrypt the file. We can also encourage and restrict content sharing to links rather than the file itself so that the source of the content does not change. Importantly, the controls and capabilities are better in the cloud so from a DLP perspective, you don’t lose data, data is not shared with anyone it shouldn’t be shared with, and it’s not accidentally deleted. Sharing and access can be monitored and reported on, providing governance controls and the necessary documentation to meet compliance requirements.
These are benefits that every business needs to thrive today. But the file server migration process can be complex and it is certainly nuanced. That’s why it’s important to work not just with IT experts and engineers but with information architecture consultants who understand business processes and regularly work with companies to maximize the use of their Microsoft services.



