In Part 1 of this post, we examined how two Microsoft solutions, Privileged Access Workstation (PAW) and Local Administrator Password Solution (LAPS), protect privileged accounts and the data and applications they use. PAW is capable of distinguishing privileged administrative accounts from normal user accounts. When a privileged account is recognized, PAW creates a hardened physical environment for sensitive tasks while preventing high-risk activity. LAPS automatically generates, encrypts and randomizes passwords based on security policies and simplifies password management.
Now, let’s take a closer look at how Microsoft Privileged Access Management (PAM) helps to secure privileged accounts. PAM is an Azure Active Directory Privileged Identity Management solution that restricts privileged access in Active Directory environments. If such an environment is compromised, PAM can retake control by maintaining a separate, bastion environment that hasn’t been compromised by malicious activity. PAM also isolates privileged account use to reduce the risk of stolen credentials.
Accessing resources within an Active Directory environment is fraught with challenges. Active Directory vulnerabilities make it easy for attackers to steal the credentials of Domain Administrators. This opens the door for unauthorized privilege escalations, as well as pass-the-hash, pass-the-ticket, spear phishing and other credential-theft attacks.
PAM is designed to stop malicious users from gaining privileged account access to various domain-joined computers and their applications. PAM also provides organizations with more visibility into those environments so they can be more closely monitored and granular controls can be enforced. This makes it possible to identify privileged administrators and understand how their accounts are being used.
PAM Set-up Steps
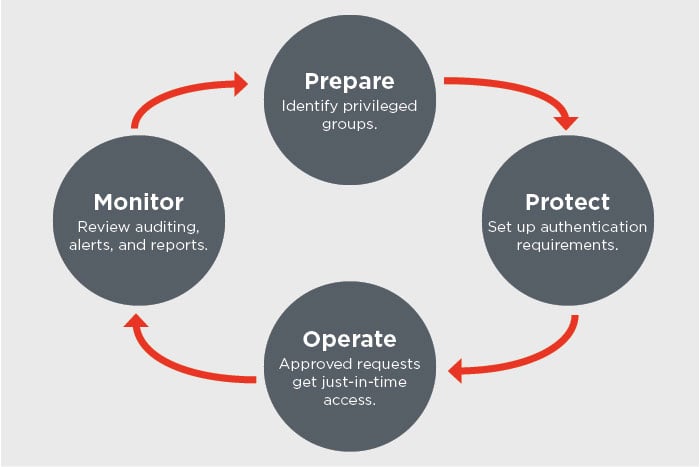
Using new capabilities in Active Directory Domain Services and Microsoft Identity Manager (MIM), PAM separates privileged accounts from an Active Directory environment. Before a privileged account is used, it must be requested and approved. Then the account is granted permission through a foreign principal group in a new bastion forest. While normal user accounts can stay in their existing forest, privileged users must move to the new bastion forest. This enables the organization to control authentication methods and when users can join a privileged group.
The next step is for the bastion forest to issue a time-limited group membership, which then generates a time-limited ticket-granting ticket (TGT). The TGT can be enforced by a Kerberos-based application or service if that application or service is in a forest that trusts the bastion forest.
PAM allows organizations to isolate and establish the scope of privileges and restrict access by requiring users to request privilege. Step-up and proof-up authentication and authorization challenges aid in the management and control elevation of administrative accounts. Additionally, PAM provides logging to show privilege requests, authorizations and subsequent events, and multiple, built-in MIM workflows can be customized according to the requesting user or role.
The AdaptivEdge team offers more than 200 years of combined experience across the entire Microsoft technology stack. Each engineer works with no more than two Microsoft solutions. This highly focused model enables all engineers to become true experts and specialists in a very specific and often complex area. Let us show you how to deploy and configure Microsoft’s PAW, LAPS and PAM solutions in a way that minimizes risk to privileged accounts.
For more information please review Microsoft PAM documentation found here.
Written and composed by our Senior Managing Partner, Stephen Soper

