Introduction
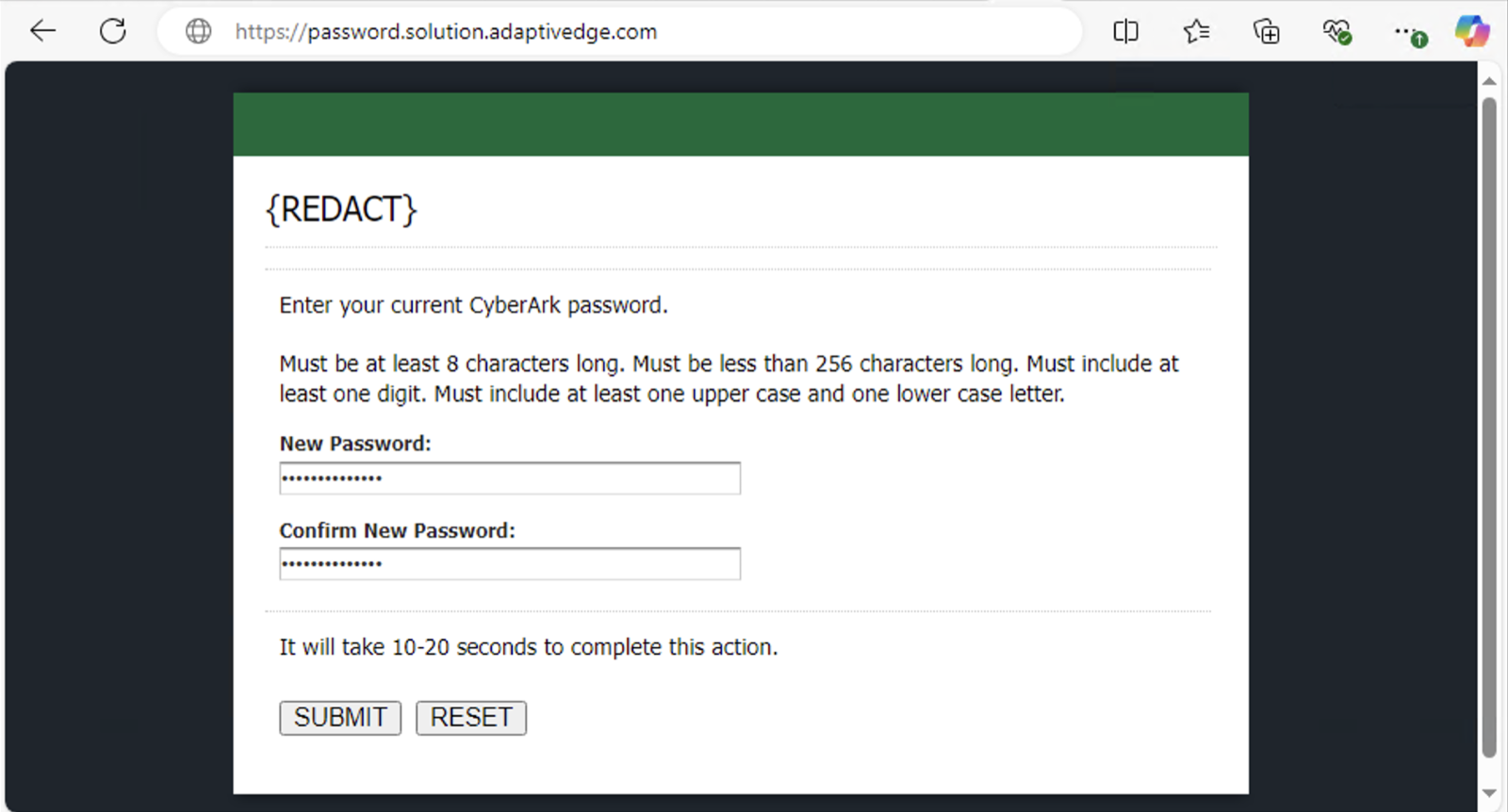
Hello, everyone! My name is Ashton Briscoe, and I am a Microsoft Security Engineer with a passion for solving complex problems and enhancing user experiences. Recently, I had the opportunity to work on an intriguing project that involved migrating a customer's identity management system from CyberArk to Microsoft Entra ID. This project presented a unique challenge: ensuring a seamless transition for users without compromising security.
Read More
Tags:
security,
Microsoft Entra
Microsoft Teams has seen a significant increase due to the ongoing coronavirus pandemic with active daily users now totaling more than 44 million users. Teams was already on an impressive growth trajectory without the impact of a pandemic forcing remote work for all information workers. There’s no doubt that Teams is a phenomenal tool for collaboration, but like any technology providing collaboration and communication, security and governance need to be an integral part of design, implementation and training.
Read More
Tags:
SharePoint,
security,
Teams,
Governance,
microsoft 365,
DLP,
sharing
Watch Affinity Workforce tackle modern security challenges with ease, utilizing the integrated and user-friendly Microsoft 365. With the heavy lifting of security already done, companies can save money and employees can focus on getting straight to the task at hand.
Read More
Tags:
security,
microsoft 365
At AdaptivEdge, we believe that security should be a part of every conversation, consultation, and solution we deliver. Our Security and Compliance experts have developed step-by-step instructions on how you can enhance the security of your Office 365 deployment.
Authored by Steve Andrews (Director Cloud Platform Services) & Raul Perez (Senior Microsoft Systems Engineer)
Read More
Tags:
Adaptive Edge,
O365,
E5,
Enterprise,
Office 365,
cybersecurity,
Microsoft,
security,
Secure Score
While the use of collaboration tools is on the rise, email remains a vital component of corporate communications. It’s also a primary vector for malware distribution and attacks on endpoint devices. Most of these attacks attempt to exploit users rather than defeat security controls. In the 2018 Survey on Endpoint Protection and Response by the SANS Institute, 53 percent of IT professionals said their organizations had fallen victim to social engineering and phishing attacks, while half said they’d been impacted by ransomware.
Read More
Tags:
cybersecurity,
security
In the military, the term “attack chain” or “kill chain” is used to describe how an attack is structured and executed, from identification of a target to selection of an appropriate weapon to the use of that weapon on the target. Reconnaissance operations are employed throughout the chain to monitor the movement and defense capabilities of the target and evaluate the impact of the attack.
Read More
Tags:
adaptivedge,
cybersecurity,
identity,
phishing,
UEBA,
cyberattack,
security
The days when users accessed corporate applications and data via desktops at the office are long past. Mobile devices enable anytime, anywhere access to both internal and cloud-based resources. The traditional network perimeter no longer exists.
Read More
Tags:
Active Directory,
adaptivedge,
microsoft azure,
cybersecurity,
Microsoft,
security