Microsoft continues to address vulnerabilities around user identity and has integrated a solution in Azure AD (currently in public preview) that enhances password policies to protect against common, weak passwords. Organizations can now configure their change/reset process to flow passwords through a sequence in which they are validated against banned passwords lists. If users attempt to use a banned password, they are notified that the password is vulnerable and will need to try a different password.
Read More
Tags:
Technology,
Azure,
cybersecurity,
Microsoft,
Azure AD
In the previous post, we discussed why every organization, regardless of how sophisticated its IT security infrastructure and operations are, needs an incident response plan. The first goal is always to prevent a data breach from happening. However, if there’s one thing we’ve learned about data breaches during the past five years, it’s that even the largest retailers, financial institutions, Internet giants and government agencies can be victimized.
Read More
Tags:
Technology,
cybersecurity,
Microsoft,
Windows Defender ATP
At AdaptivEdge, we believe that security should be a part of every conversation, consultation, and solution we deliver. Our Security and Compliance experts have developed step-by-step instructions on how you can enhance the security of your Office 365 deployment.
Authored by Steve Andrews (Director Cloud Platform Services) & Raul Perez (Senior Microsoft Systems Engineer)
Read More
Tags:
Adaptive Edge,
O365,
E5,
Enterprise,
Office 365,
cybersecurity,
Microsoft,
security,
Secure Score
Many organizations have taken a more proactive approach to IT security rather than waiting for something bad to happen. Recognizing the immense cost of a data breach (an average of $3.86 million) and the time it takes to contain a breach (an average of 69 days) these organizations follow best practices and deploy security tools that reduce risk related to malware, zero-day exploits and other threats.
But that’s not enough.
Read More
Tags:
Technology,
cybersecurity,
Microsoft
There isn’t much an organization can do to reduce the number of security threats it faces on a daily basis. Hackers will be hackers. They constantly develop new techniques and tools that allow them to carry out as many attacks as possible. However, organizations can make the job of a hacker more difficult by reducing the attack surface.
Read More
Tags:
cybersecurity,
Microsoft,
Secure Score,
Attack Surface,
Windows Defender ATP
While the use of collaboration tools is on the rise, email remains a vital component of corporate communications. It’s also a primary vector for malware distribution and attacks on endpoint devices. Most of these attacks attempt to exploit users rather than defeat security controls. In the 2018 Survey on Endpoint Protection and Response by the SANS Institute, 53 percent of IT professionals said their organizations had fallen victim to social engineering and phishing attacks, while half said they’d been impacted by ransomware.
Read More
Tags:
cybersecurity,
security
In Part 1 of this post, we examined how two Microsoft solutions, Privileged Access Workstation (PAW) and Local Administrator Password Solution (LAPS), protect privileged accounts and the data and applications they use. PAW is capable of distinguishing privileged administrative accounts from normal user accounts. When a privileged account is recognized, PAW creates a hardened physical environment for sensitive tasks while preventing high-risk activity. LAPS automatically generates, encrypts and randomizes passwords based on security policies and simplifies password management.
Read More
Tags:
adaptivedge,
cybersecurity,
PAWS,
identity management,
privileged accounts
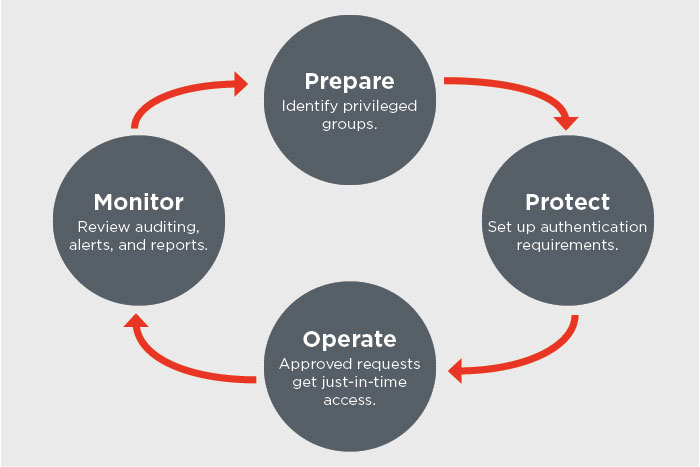
Over the last several posts, we’ve been discussing the need for a modern security strategy that protects the “identity perimeter” with special emphasis on securing privileged accounts. We also explained how user and entity behavior analytics can break the cyberattack chain by identifying and mitigating insider threats and compromised user credentials.
Read More
Tags:
adaptivedge,
cybersecurity,
identity management,
privileged accounts,
data loss prevention,
identity perimeter
In the military, the term “attack chain” or “kill chain” is used to describe how an attack is structured and executed, from identification of a target to selection of an appropriate weapon to the use of that weapon on the target. Reconnaissance operations are employed throughout the chain to monitor the movement and defense capabilities of the target and evaluate the impact of the attack.
Read More
Tags:
adaptivedge,
cybersecurity,
identity,
phishing,
UEBA,
cyberattack,
security
In our last post, we explained that identity has become the new perimeter in today’s cloud-based, mobile-enabled environment. It’s no longer possible to maintain IT assets and applications behind a firewall. Organizations must implement robust identity management and authentication mechanisms to ensure that only authorized users gain access to resources.
Read More
Tags:
Active Directory,
adaptivedge,
Azure,
cybersecurity,
privileged accounts,
Microsoft